CGI Cyber Security
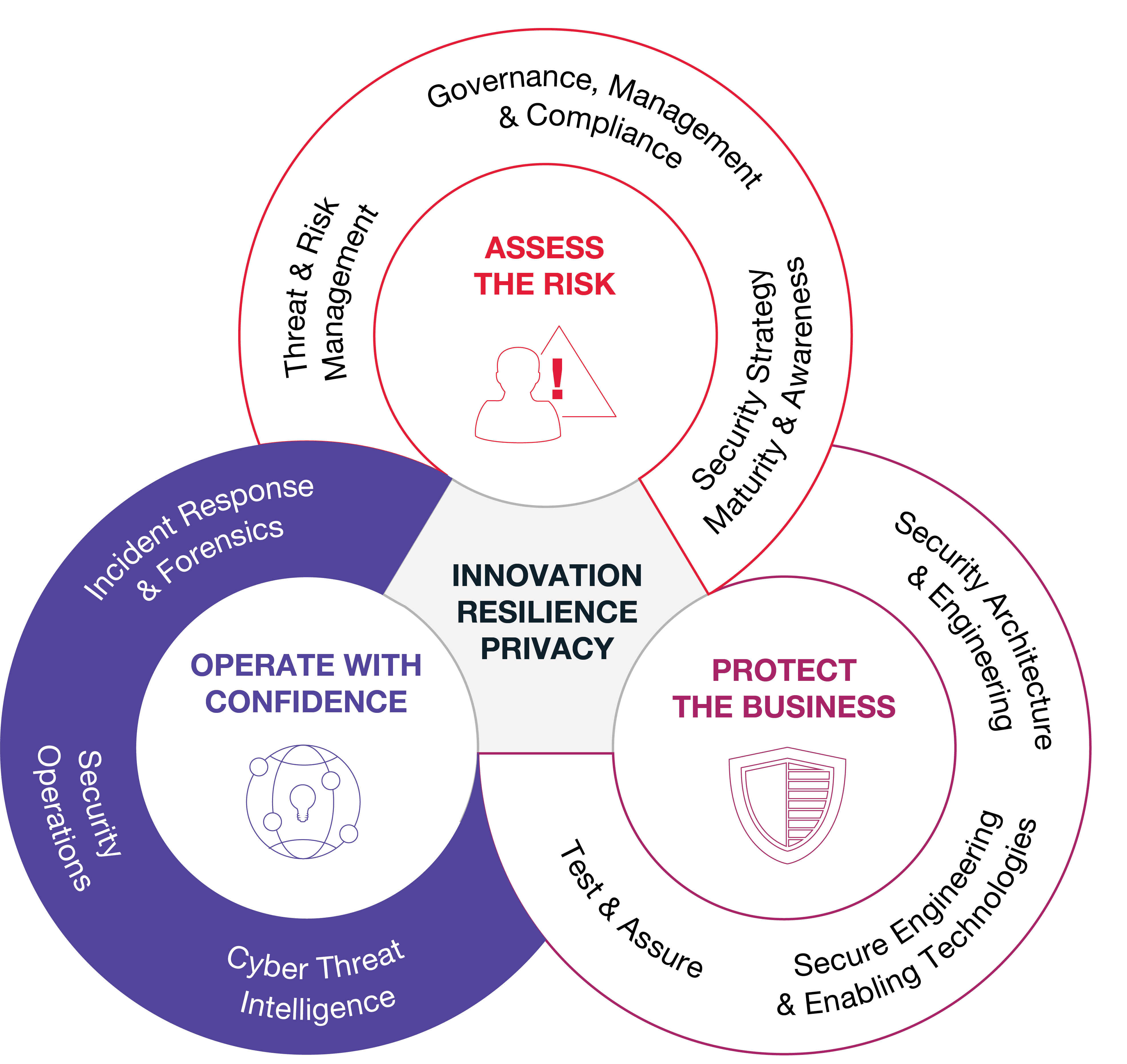
Cyber security is part of everything we do. We have over 1,700 cyber security experts globally with one of the largest cyber security practices in the UK helping clients manage complex security challenges with a business-focussed approach, protecting what is most valuable to them.
Learn moreLearn more